I’ve been talking to a number of educational institutes recently who are laser focused on security and in this current climate I think this approach is entirely justified. With more students and educators learning remotely the ability to protect devices and content simply from being behind an institutional firewall is harder than ever.
Background
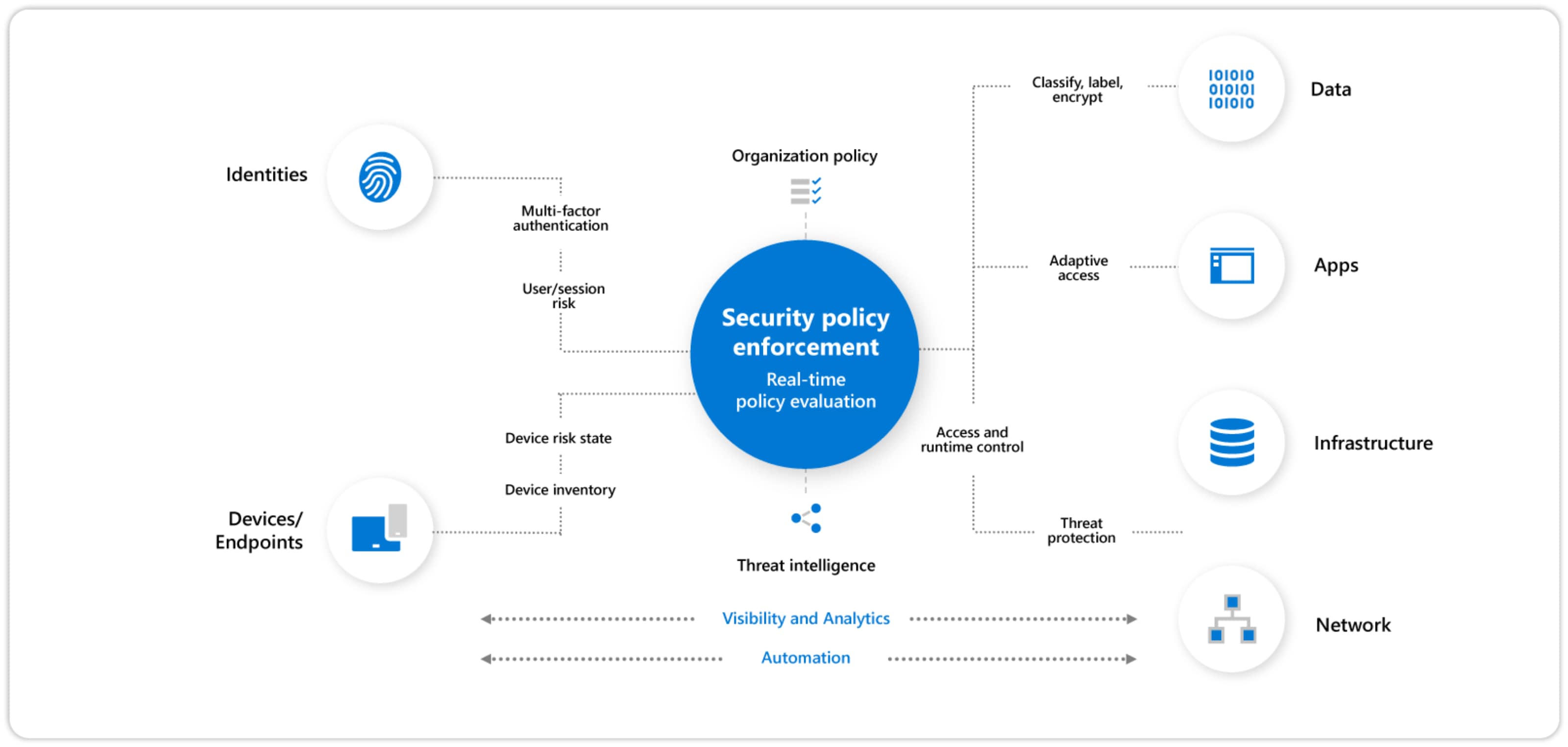
The Microsoft Zero Trust Security Model and Framework is the rulebook on best practice when it comes to implementing an holistic approach to security and has three core pillars as the foundation:
- Verify explicitly
- Always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies.
- Use lease privileged access
- Limit user access with just-in-time and just-enough-access (JIT/JEA), risk-based adaptive polices, and data protection to help secure both data and productivity.
- Assume breach
- Minimize blast radius and segment access. Verify end-to-end encryption and use analytics to get visibility, drive threat detection, and improve defenses.
So if you’re wondering how Zero Trust is actually defined, here’s a good overview:
Instead of assuming everything behind the corporate firewall is safe, the Zero Trust model assumes breach and verifies each request as though it originates from an open network. Regardless of where the request originates or what resource it accesses, Zero Trust teaches us to “never trust, always verify.” Every access request is fully authenticated, authorized, and encrypted before granting access. Microsegmentation and least privileged access principles are applied to minimize lateral movement. Rich intelligence and analytics are utilized to detect and respond to anomalies in real time.
Zero Trust Security Model and Framework | Microsoft Security
It’s worth noting the definition above aligns with my opening sentence: you simply cannot assume that everything behind the corporate firewall is safe and building on this you absolutely cannot assume that your remote educators or students are operating from within a secure environment. Given education is about supporting all learning styles, if you’re a visual learner and learn through images instead of text, this should help:
Protecting Against Crypto-locker Style Attacks with Controlled Folder Access
The best way to implement a robust Zero Trust framework is to leverage the four arms of Microsoft 365 Defender services. Some of these services have changed names recently but I found this visual quite helpful to understand the four arms of protection:

Again, if your learning style is more ‘hands on’ (kinesthetic) then this interactive click through guide may interest you! Controlled Folder Access is part of the Microsoft Defender for Endpoint suite of tools and can be defined as:
Controlled folder access helps protect your valuable data from malicious apps and threats, such as ransomware. Controlled folder access protects your data by checking apps against a list of known, trusted apps.
Protect important folders from ransomware from encrypting your files with controlled folder access | Microsoft Docs
In short, this protects your data by only allowing trusted and approved apps to access defined folders. Conversely, non-authorised apps (that would typically include malware) simply cannot write to your protected folders, preventing an unauthorised encryption taking place and a ransom being demanded for return of access.
In the context of my recent discussions this has been particularly important as many education customers are starting to take greater advantage of the sync feature in SharePoint Online and Microsoft Teams so that folders and files in the cloud are available on their device even in an offline capacity. If this is news to you, definitely check out the guide here but essentially anywhere in SharePoint or Teams you see the sync icon you can save that content to your device:
The impact is this folder then shows up in your Windows File Explorer (very similar to the traditional network file shares e.g. D:\ or S:\ etc):
Controlled Folder Access: a few details
Windows system folders are protected by default, along with several other folders:
c:\Users\<username>\Documentsc:\Users\Public\Documentsc:\Users\<username>\Picturesc:\Users\Public\Picturesc:\Users\Public\Videosc:\Users\<username>\Videosc:\Users\<username>\Musicc:\Users\Public\Musicc:\Users\<username>\Favorites
You can add any custom folders you like, so in a scenario where colleagues are using the SharePoint or Teams sync to collaborate, it could be a great idea to protect those folders so that a ransomware attack can not encrypt that content locally and then have it sync back to the SharePoint / Teams site and impact all users. If you want to review or change the list of protected folders with Controlled Folder Access it’s simple:
- On your Windows 10 device, open the Windows Security app.
- Select Virus & threat protection.
- Under Ransomware protection, select Manage ransomware protection.
- If controlled folder access is turned off, you’ll need to turn it on. Select protected folders.
- Do one of the following steps:
- To add a folder, select + Add a protected folder.
- To remove a folder, select it, and then select Remove.
Controlled Folder Access is supported on any version of Windows 10 1709 or later and also on Windows Server 2019
The list of apps that can write to your controlled access folders are trusted and there is a default list managed by Microsoft based on their prevalence and reputation and those that have never displayed any behaviour deemed malicious. However, you can also manually approve an application to write to these folders if required and whilst this can be done manually by each end user, best practice would be to manage this centrally by policy, ideally with Microsoft Endpoint Manager (MEM)
Useful Further Reading
I mentioned at the start of this blog that many of my recent conversations with educational customers have been around security, and in writing this blog I did a quick search on Windows 10 Controlled Folder Access and saw that a lot of people have written blogs about this topic. I’m going to link to a few here (in no particular order):
- I mentioned above that the best way to implement this consistently across your educational institute is via policy – either Microsoft Endpoint Manager or PowerShell. I’d recommend MEM for this job to be honest
- All events recorded from access to protected folders are stored in the Event Log. This is worth checking out if you need to troubleshoot:
- Some cautions about needing to have a plan when you’re implementing Controlled Folder Access – always worth considering!
Of course, even best laid plans can sometimes be thwarted so having a clear strategy on recovery from an attack is critical. This guide on how to recover from a ransomware attack in Microsoft 365 should be critical pre-reading for all IT Administrators in advance of an attack. You’ll be thinking a lot clearer with less stress induced brain fog if you’re reviewing this in advance, compared to reactively trying to fix your environment after a breach.
I hope this was useful and feel free to drop any feedback in the comments down below.

















